Network access control (NAC) is a security software that businesses can use to control the amount and level of access to their networks.
According to WiFi engineers and IT security professionals, NAC is the most recommended solution to solve the security challenges of today's BYOD and IoT-filled network environments.
The top benefits of network access control include increasing network visibility, reducing cyber threats, and drastically improving network performance.
So, whether you are worried about your next big network security audit or IoT devices overrunning your network, network access control can help.
In this blog you'll learn:
- How does network access control work?
- Why invest in a NAC solution?
- NAC Use Cases
- How to prepare and implement a NAC solution?
- How to choose the right NAC solution?
How Does Network Access Control work?
In order to fully appreciate the advantages of network access control, it is crucial to have a clear understanding of how it functions.
The license of the NAC solution that you bought would be uploaded on to either a physical server or a virtual machine (aka a virtual server).
However, you will need a professional certified in the implementation of that product to get things rolling—NAC isn't something that you can just download and carry out yourself.
Then, network access control works by utilizing your Active Directory (or other directory system/multi-authentication platforms) and allows you to create a list of rules—or policies— that it enforces on each device that attempts access to your network.
That way you can provide different levels of access to the network based on who you are and what you need.
For example, if you work at a college and you're a network admin, you would have the most access to the network, while a CMO would have less access but still more than a college student, and a college student would have more access than a guest to the network.
Think of NAC as your bouncer and your network is the nightclub that everyone wants to get into. The bouncer is looking at your ID, making sure that you're on the list, seeing if your outfit adheres to the dress code, etc. Then, depending on your level of celebrity status, determines what level of the club you're allowed to go to—all the way up to the VIP lounge.
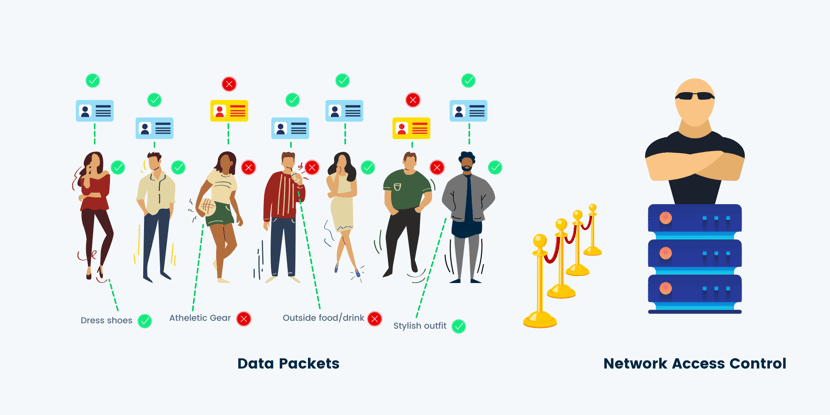
This is a valuable solution for businesses who have a lot of people wanting to get into their "Club Network".
Why Invest in a NAC Solution?
Many organizations tend to tackle network security in pieces—a firewall here and an anti-virus solution there. However, using completely separate systems for managing access permissions creates mass disorganization and a lot of administration overhead.
Network access control allows for a complete centralized approach to the security of your network.
In the old days of wired connections and computer labs, security policies were strict and easy to maintain. You knew what devices you had to support and where they were because you purchased them, and they never moved.
However, with the increase of IoT and BYOD initiatives, the increase of security and cyberthreats have also increased.
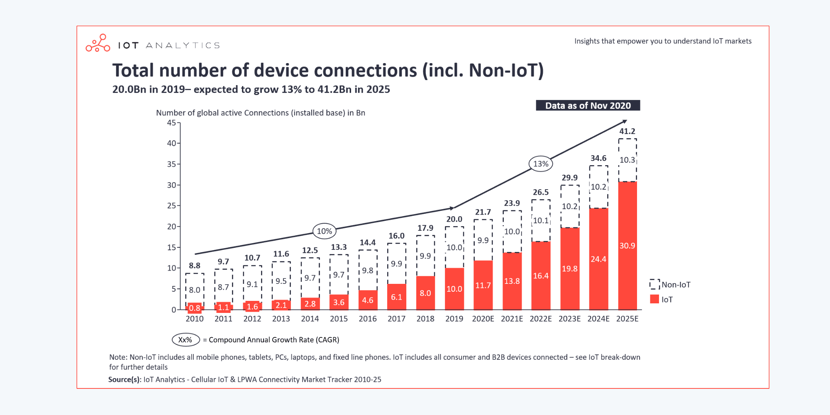
And with great technological power comes great network responsibility.
IT teams now have a great challenge: "How can I monitor network traffic for malicious behavior and still provide scalable access to the network?"
NAC is the best answer and should be the security solution that is at the top of everyone's security must-haves list.
Here are the 3 top reasons why you should invest in a network access control solution:
- To gain visibility on the network
- To reduce cyber threats
- To improve network performance
1. To Gain Visibility on the Network
Managing access to your network starts with having proper visibility.
If you can’t see who or what is accessing your network and where they’re trying to go, then it’s going to be difficult to deliver a reliable and secure network experience.
Network access control allows you to identify who, what, where, when, and how an end-user or device is accessing your network.
- Who: Who is the end-user and are they a known user inside of your active directory?
- What: What is the end-user trying to access on your network?
- Where: Where are they connecting to the network?
(The office, the cafeteria, hotel room, dorms) - When: When are your end-users or IoT devices accessing the network?
Knowing this will also give you insights into when they are most active and least active, helping you to distribute bandwidth more efficiently. - How: How your end-users are accessing your network (smartphones, laptops, tablets)?
This also includes what IoT devices/systems are accessing your network (security cameras, vending machines, HVAC, scanners, printers, POS systems, etc.)
With each employee bringing on average 3 mobile devices with them—not to mention all the IoT devices that your business might have—it's critical to have as much visibility on the network as possible.
2. To Reduce Cyber Threats
Cybercrime is up 600% due to the COVID pandemic, according to Purplesec's 2021 trend report.
Any network security vulnerabilities that can be easy-picking for a malicious actor. Network access control helps reduce cyber threats in two ways: role-based access control and limiting the scope of malware.
A feature of NAC is role-based access control, which assigns the correct corresponding role for each user/device.
Role-based Access Control ( also known as RBAC) is a security model where users are given assigned roles based on their role in the company.
If you've ever used parental controls for monitoring a child's internet use, RBAC is similar but on a more finite and larger scale.
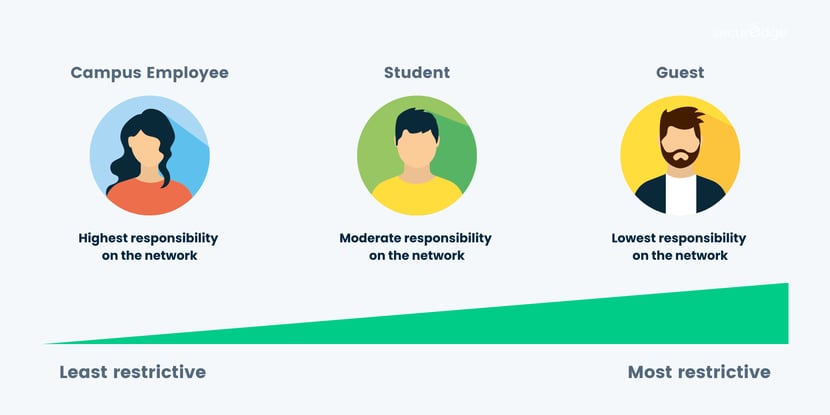
With pre-determined policies and assigned roles, role-based access control allows you to customize the right wireless experience for each type of end-user/device accessing your network.
When reducing cyber threats, NAC consists of two key steps: authentication and authorization.
Authentication is when the system verifies the based on credentials, while authorization is when the system accepts or denies access based on the policies in place. A user needs to pass both steps in order to achieve the access requested to the network.
The process of assigning and enforcing security policies based on those roles (aka endpoint integrity) , allows you to control the behaviors of all of the devices trying to access your network.
The second way that network access control increases security is by limiting the scope of malicious behavior.
According to Kaspersky: 360,000 new malicious files are being downloaded accidentally by employees everyday! So even an authorized user can accidentally have turned their device rogue by opening up a bad email, which can spread throughout the network without proper access controls.
Network access control can ensure intellectual property and sensitive data are protected from unauthorized use, capture, or modification. In other words, even if the device/user has access to a certain piece of information inside the network, if they are prevented from "acting improperly" with it (for example, copying and pasting that information to another device).
So network access control ensure that your end-users are adhering to the terms of service, as well as making sure that viruses aren’t being unintentionally (or intentionally) spread across your network.
3. To Improve Network Performance
A benefit of network access control that is not often thought about is how it can improve the performance of your network.
Oftentimes, businesses add multiple SSIDs for staff as a way of getting around implementing a NAC tool. It can do the job at a basic level (without the granularity of NAC), however, every SSID that you put into the air takes up bandwidth. So each time you give out a different password for a different end-user on your network, you're severely crippling the performance of everyone.
With the role-based access control feature of a NAC solution, you can have all staff be on the same SSID because you have policy enforcements based on their role within the company. For example, you can give the IT team more access to the network than the Chief Marketing Officer.
Each SSID that you reduce will give you, roughly, a 10% of bandwidth back. In instances of more complex environments—a hospital, for example— might use up to 7 or 8 SSIDs. But by implementing a NAC solution, we've given some companies 40-50% bandwidth back just by taking out the overhead created by those additional SSIDs.
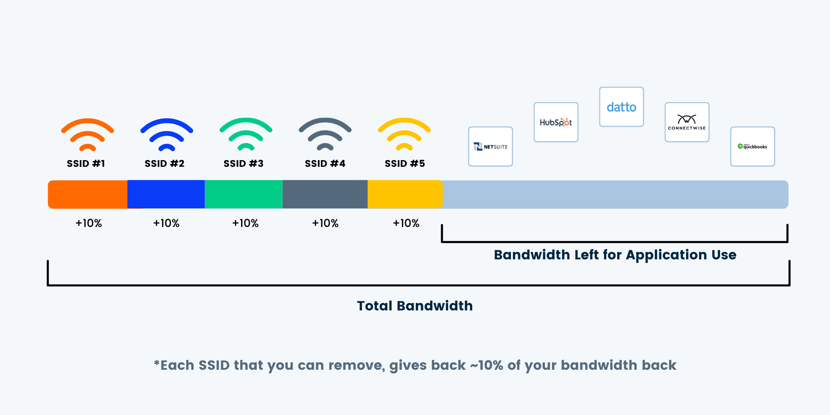
You can also create role-specific bandwidth contracts that will limit or reserve rates depending on your role. This is used to give certain applications or certain users priority over your traffic over others, like an employee over a guest or a business application over iTunes or Snapchat.
Network access control is not only a security enhancement, but also a performance enhancement.
NAC Use Cases
There are different use cases for NAC due to the versatility of this security solution. It solves multiple problems that you might have use for. Here are the top 5 use cases for NAC:
NAC for Guests |
NAC can make sure that your guests have access to the internet but not access to your entire network. Segmenting guests from employees is important because guests create more variables than employees. |
NAC for BYOD |
In order to increase employee productivity and reduce device cost, we've begun implementing BYOD initiatives where employees can use their own devices at work. NAC for BYOD ensures ensures compliance for all devices and determines which endpoints and what data that device has access to. |
NAC for Remote Work |
Due to the Covid-19, we now have a more remote workforce that is increasing the demands of VPN as way to access your network from their home. Since network access control allows you to layer levels of authentication and authorization, it can protect your network by restricting access to credentialed employees who are trying to access with an unauthorized device. |
NAC for IoT |
Everyone remembers the 2014 Target Hack. where cyber thieves broke into their network and stole customer financial data. However, did you know -- the hackers attacked via their HVAC unit? Your IoT devices serve as additional points of network access and need to be monitored. Network access control tools can take an inventory of IoT hardware and limit their access to the network. |
NAC for Incident Response |
When it comes to minimizing the scope of a cyber attack, some NAC solutions are built on AI software and have the ability to automatically and remotely shut off the rogue IoT device until an IT team can resolve the problem This is safeguarding valuable data and saving businesses a lot of money. |
How to Prepare and Implement a NAC Solution
Before purchasing anything, it's important to plan for the entire implementation of your NAC solution from start to finish. You don't want to install a NAC tool before knowing what the process looks like and what information you should gather ahead of time.
Here are the 4 main steps when implementing a NAC solution:
-
Know Your Endpoints
-
Check Update your Directory System
-
Determine and Apply Permissions
-
Keep Everything Updated
1. Know Your Endpoints
Great strategies always start with a bit of planning. The first step when beginning a NAC solution is to perform a survey of every computer, phone, IoT device, and server that is considered an endpoint to your network.
Depending on the size of your business, this can be hard work on the front-end, but without this data, your NAC system cannot be truly effective if it doesn't have a list of the devices that you know are entering your network.
2. Check and Update your Directory System
Considering what we discussed about role-based access control previously, a NAC solution needs to determine how much authorization each person should have.
Therefore, you must decide how you will manage the different roles within your business. You can do this by verifying the user identities that can be found in your existing directory system—usually its Active Directory by Microsoft—and then determine how the roles should be configured.
3. Determine and Apply Permissions
Determining permissions will vary across industries and business preferences, however, the Principle of Least Privilege (PoPL ) is a tactic that many security experts recommend. PoPL prescribes that access be restricted at the lowest possible level, meaning that you only give the access needed for an individual to complete their job.
Integration between your NAC tool and the existing directory should be simple enough. You just have to make sure that every employee is registered as a user in the NAC tool so that their network activity can be monitored.
4. Keep Everything Updated
Keeping things fresh and updated is the most crucial part of any business' network strategy.
Making adjustments to everything from your Active Directory to the permission policies of your NAC solution as you experience employee turnover or growth, will ensure that your network access control tool stays effective.
How to Choose the Right NAC Solution?
There are two questions we receive all the time about network access control: What NAC features should I be looking for and which NAC solution is the best for my business? We're here to answer these questions, however, there will be a few factors to consider that might affect the network access control product that you pick.
Factors that will affect your NAC solution:
- Maturity of your current security strategy
- Goals for bringing NAC into your network
- The granularity of enforcement policies
- Organization's budget
- CAPEX or OPEX preferences
Network Access Control Solution Checklist
When it's time to purchase a NAC solution and you are discussing your options with multiple vendors, here's a list of question you should have handy:
- What kind of network visibility does the solution offer my business?
- Can it integrate with my existing infrastructure?
- How adaptable is it for future infrastructure changes?
- How much does it enforce?
- Does it fulfill my compliance needs?
- How complex is the deployment process?
- Does the solution offer real support and not just community-based support?
- How much will the complete NAC solution cost?
- Are there any proactive tools included?
Top NAC Solutions
In no particular order, here's a list of the best network access control tools out there and the vendor that provides the product:
- Cisco's Identity Service Engine
- Fortinet's FortiNAC
- Aruba's ClearPass
- ForeScout's CounterACT
- Pulse Secure's Pulse Policy Secure
Our NAC Recommendation: Aruba's ClearPass

Aruba Dashboard Source: Aruba
The main reasons why we recommend Aruba's ClearPass Policy Manager as the NAC tool for all our customers is:
- Security-first approach - Aruba is known as a strong security vendor in general because of how they build their products. Their APs come with a built-in firewall and their Policy Enforcement Firewall gives them the ability to do role-based access control and offer more dynamic segmentation of the network.
- Super granular enforcement policies - ClearPass has the most granular policy enforcement. Not only can you create policies on user role and device type, but also device health, traffic patterns, location, and time of day.
- Onboarding Scalability - ClearPass Onboard, which enables users to self-onboard multiple devices while automatically profiling the device for secure BYOD onboarding. And what's unique about their onboarding tool is that it creates a custom certificate for each device and is "married" to that device. So even if a tech-savvy user were to try to steal that certificate of authorization from one device and transfer it to another device, it wouldn't work.
- Vendor-agnostic - ClearPass is vendor-agnostic, meaning that any business can use it on their existing infrastructure and not have to worry about compatibility issues.
Final Thoughts
Your security strategy should be a centralized approach in order to best manage all endpoints from external threats. Network access control offers you a way to define your security policies and automatically apply your rules to all network users. So even if a user is authorized to use the network, NAC can still protect your network from potential threats from that device.
It's important to note that network access control requires extensive training, the right certifications, and experience working with the software. An IT professional will need to know security and authentication on wireless, certificate-based authentication, VPN technologies, directory database services, etc. Working with a trusted service provider is always recommended when it comes to implementing a security strategy for your network.
If you have questions about NAC or would like to discuss implementing your security strategy with network access control, feel free to contact us here.