One of the biggest challenges IT managers face today is visibility. In most cases, you don't own the devices coming onto to your network and with your users accessing the network from inside and outside of your business, (yes, even remotely), it's hard to determine where to start when you run into problems.
In today's Whiteboard Wednesday, Senior Network Engineer Michael McNamee dives into how you can effectivelysee what's happening on your network and control it, using Role-Based Access Control.
Key Takeaways
- Role-Based Access Control (RBAC) or role-based security is a method of assigning specific rules or policies to individual users, or groups of users, that are connecting to your network.
- RBAC is needed to determine who was accessing the network, how they were accessing it, and where they were accessing it from, and then apply policies to control that level of access.
- Benefits:
- Granular control of user/device access
- Provides necessary resources denies unnecessary resources
- Improves performance
Video Transcript
Hey there, SecureEdge fans, and welcome to another edition of our Whiteboard Wednesday.In this session today, we're going to be talking about role-based access control, what it is, and what are some of its benefits.
Role-based access control came about as an answer to the question that everybody was asking as they installed their first wireless networks, and that question was, how do we secure our network and limit access to it?
What is Role-Based Access Control?
Role-based access control was introduced to determine who was accessing the network, how they were accessing it, and where they were accessing it from, and then apply policies to control that level of access.
Role-based access control, or RBAC as we call it here, is in simple terms the security process of assigning specific rules or policies to individual users, or groups of users, that are connecting to your network.
For instance, applying a policy for access to faculty members different than what is granted for student access to your network.
Or it could even be assigning a policy to the employee role differently than what a guest or visitor would be granted when they come into your network.
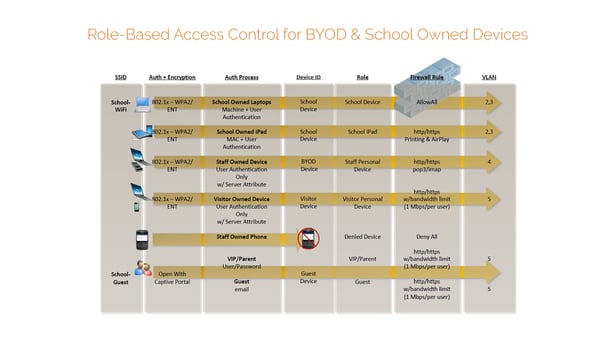
We're showing a diagram here of what role-based access control and how it's applied. To give you an idea, we're using a school wireless network as in the example.
Click on the diagram to view a larger image.
So we have two SSIDs. We have a school Wi-Fi, we have a school guest. In the diagram, you can see that through different levels of authentication, we can apply a role to that user or device and then apply different policies and different levels of access to the network.
Even with the school guest SSID, we have different authentication methods, and based on those authentication methods, we're applying different levels of access to the network.
How can you apply it to your network?
So now that we know what a role-based access control is, let's touch on how it can be applied in your network.
One of the first things that we need in role-based access control is to understand who the user or the device is.
And there several ways of doing this. One could be just through simple Mac authentication, or we could do device fingerprinting.
So we can understand that this is a mobile phone versus a laptop or a tablet or even a device owned by the school.
Or it could be something even as simple as deriving a role based on someone's group membership in active directory.
So once the identity is known, we can apply a role to that user or device, and then once the role is known, we can apply a firewall policy or an ACL to that role.
The policies can be as restrictive or as loose as you want it to be. It's totally up to you.
So one of the key takeaways from this is to understand that the process happens automatically in real time. It's imperceptible to the end-user. There's no end-user intervention. They have no idea that this is even going on.
So as simple as this sounds, you'd be surprised at how many wireless LAN products are incapable of applying or doing role-based access control.
What are the benefits of RBAC?
There's lots of benefits to having the capability of doing role-based access control.
One, it gives you granular visibility that you need to securely support your mobility in today's wireless environment.
Second, role-based access control ensures that your users and guests have what they need and nothing more. It keeps them and your network safe.
Third, there's some performance improvements when doing role-based access control. When introducing role-based access control in your network, because we're denying extra applications or services and traffic at the point of entry into your network, you're going to gain back some valuable bandwidth.
All right, everyone, I look forward to your comments as well as any questions that you have about role-based access control. Thanks for watching today, and we'll see you again for another edition of Whiteboard Wednesday. Take care.
If you have any questions about role-based access control and would like to discuss them in detail, please contact us here!