In our dealings with technology leaders at schools, universities and hospitals there are many different opinions as to how they would each go about solving an IT problem or challenge. Those who are successful at solving issues like BYOD, 1:1, web filtering or the simple lack of available bandwidth do have one thing in common: A need for updated infrastructure.
Firewalls are a key piece of infrastructure for any of those IT leaders in securing their organization’s sensitive data and reducing the risk of attack. With that in mind, here are 11 Features to Look for in Your Next Firewall:
1. Identify and control applications on any port
With the rise of mobile devices and the multitude of operating systems, application development has also become easier, which opens the door for less quality control prior to applications being made available to the public. Since application developers no longer stick to the old standard of port/protocol/application mapping, more applications are now capable of operating on non-standard ports or can hop ports (e.g., Facebook or Yahoo! instant messaging applications, peer-to-peer file sharing like UTorrent, or VOIP). Today’s younger users are increasingly savvy enough to force some applications to run over non-standard ports (e.g., MS RDP, SSH). While the 4-year-old at our house racing through the gaming applications may not be at that level just yet, the point is that children are growing up with these devices in their hands while we were stuck sitting with a Commodore 64 or a Tandy 80, so imagine what they’ll be capable of in 20 years.
2. Identify and control circumventors
Most organizations have network security policies and controls designed to enforce those policies they have spent so much time trying to implement. Villainous hackers use proxies, remote access, and encrypted tunnel applications which specifically used to circumvent security controls like firewalls as they attempt to attack networks. Without the ability to control these circumventors, organizations cannot enforce their security policies and thus expose themselves to the very risks they imagined their controls would prevent. Your next firewall solution must be capable of dealing with these types of circumventors while also ensuring the application intelligence is regularly updated.
3. Decrypt outbound SSL
Today, more than 15% of network traffic is actually SSL-encrypted. In some of the more security-conscious industries like financial services, that number is more than 50%. Given the increasing adoption of HTTPS for many high-risk, high-reward applications and users’ ability to enable SSL on many websites, network security teams are like cars traveling down the interstate changing lanes without looking back and no rear view mirrors - a huge blind spot has been created. Your next firewall must be capable of decrypting and inspecting that SSL traffic and also be flexible enough to bypass selected segments of SSL traffic via policy. An example here would be web traffic from a healthcare organization - huge liability and data would be exposed to risk.
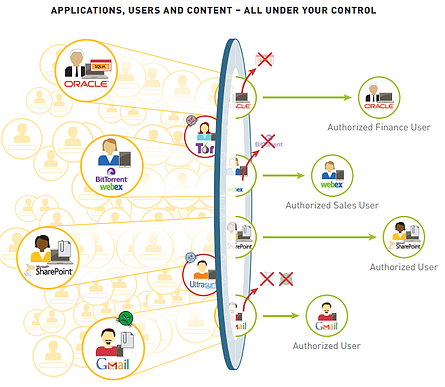
4. Provide application function control
Many applications have significantly different functions, presenting different risk profiles and value of good and bad. Some examples of this include WebEx vs. WebEx Desktop Sharing and Yahoo! Instant Messaging vs. the file transfer feature. In regulated corporate IT environments, or in organizations heavily dependent on their sensitive intellectual property, this is a significant issue. (Think about Coca-Cola’s original recipe being compromised online). Your next firewall must continually evaluate the traffic and watch for changes - if a different function or feature is introduced during the session, the firewall should note it and perform a policy check, while maintaining full functionality.
5. Scan for viruses and malware in allowed applications
Enterprises continue to adopt collaborative applications hosted outside the physical locations. Whether it’s hosted Sharepoint, Box.net, Google Docs or Microsoft Office Live, many organizations have a requirement to use an application that shares files - a potential high-risk threat from an attack. Many infected documents are stored in collaboration applications, along with some documents that contain sensitive information (e.g., customers’ personal information) that should not be exposed to the outside world.
6. Deal with unknown traffic by policy
There is always going to be unknown traffic and it will always represent significant risks to any organization, large or small. There are several important elements to consider with unknown traffic- it can be minimized, custom applications can be easily characterized so they are “known” in any network security policy and having predictable visibility and policy control over traffic that remains unknown. Your next firewall must attempt to classify all traffic, which provides a positive enforcement model (default deny). Solutions with a negative (default allow) model allows all unknown traffic. In that case, what you don’t know will indeed hurt you - so “allow all” should not be the foundation of your policy structure.
7. Identify and control applications sharing the same connection
Applications share sessions. To ensure that users are continuously using an application “platform” such as Google, Facebook, Microsoft or Salesforce, application developers integrate many different applications - which often have very different risk profiles and business value. To better explain, here’s an example with Gmail, which has the ability to spawn a Google Talk session from within the Gmail user interface. These are fundamentally different applications and your next firewall must recognize that and enable the appropriate policy response for each of them.
8. Enable the same visibility and control for remote users
Users are increasingly outside the four walls of the school, university or hospital. A significant portion of the enterprise user population is now capable of working remotely and they expect to connect to their applications via WiFi, wireless broadband or by any means necessary to complete their job duties. Regardless of the location of the user and the network they are accessing (home, library, coffee shop) your internal network, or even where the application they’re employing might be, the same standard of control should apply. If your next firewall enables application visibility and control over traffic inside the four walls of your enterprise but not outside, it misses the mark on some of the most risky traffic.
9. Make network security simpler
Many enterprise businesses struggle with incorporating more information feeds and more policies and more management into already overloaded security processes and people. In other words, if teams can’t manage what they’ve already got, adding more management, policies and information doesn’t really help the cause. Given that typical firewall installations have thousands of rules, adding thousands of application signatures across tens of thousands of ports is going to increase complexity by several orders of magnitude. (Doesn’t that thought make your head hurt?) Your next firewall must apply policy based on the user and application which significantly simplifies policy modeling and management. (May want to check and see if this is a feature that other pieces of your network infrastructure allow as well - would make integration much easier).
10. Deliver the same throughput and performance with application control fully activated
Many enterprises struggle with what many consider to be a forced compromise between performance and security. Previously, enabling network security features meant turning down throughput and performance. If your next firewall is built the right way, this compromise isn’t necessary. Given the requirement for computationally intensive tasks like application identification that are performed on high traffic volumes with low latency, your next firewall must have hardware optimized for specific tasks such as networking, security and content scanning and perform all those tasks without sacrificing speed or safety.
11. Price or Cost
So many times we go out looking for a solution but also have a budget in mind. The goal is to get the most features at the lowest possible price. It happens when you’re buying cars, toys and even groceries. So, when considering your next enterprise-grade firewall solution, it’s important to remember the cost associated with NOT moving forward. How much tolerance do you have for price vs. cost? Risk can come in all shapes and sizes, but if you have a solution in place that not only protects your organization but helps you sleep easier at night knowing that sensitive data and your network are safe from attack certainly has to be worth any extra upfront costs.
There are a number of solutions in the marketplace now that handle the above scenarios and they have various price tags attached to the physical appliance. When it comes to firewalls, we recommend Palo Alto Firewall, because it’s a complete solution that contains all the above features. If you would like a free demo or just some more information on Next Generation Firewalls you can contact us here. Also check out the great eBook below for more information.






