Imagine for a moment that you are back in elementary school and have just been awarded the orange sash and badge, making you an official Safety Patrol Officer! White gloves and whistles may have stopped your peers from crossing the street but those adornments don’t do much in the way of halting to peer-to-peer file sharing on your hospital wireless network.
Horrified as you shake off that nightmare and fast forward back to present day, you sit reviewing more about BYOD Policy and Security in Healthcare so that you can keep your knowledge current and your career on the right track. You still care about safety, you want to allow employees and guests the privilege of stepping on board to access the hospital wireless network, but you also have major concerns about privacy, lost data and even worse - lost employment. That’s a perfectly normal reality with the growing BYOD trend at work.
The mistake is in trying to create additional roadblocks to prevent BYOD implementation. Additional risk factors can now be mitigated. By placing the right network solutions in the right places, your BYOD policy and security demands can be met and successfully implemented.
Here are some keys to BYOD Policy and Security in Healthcare and as an added bonus - ways to prevent that dreaded orange sash from coming out of retirement.
1. Prioritize Application Traffic
Electronic Health Records (EHR) applications are mission-critical at a medical facility, so giving those applications maximum priority instead of having your resources drained by social applications is a good place to start. You can also establish fair sharing and usage controls that prioritize sensitive data traffic without hampering the patient’s more social experience while connecting to the healthcare wireless network. Your ultimate goal should be to set up your network to provide consistent access to mission-critical resources through fast delivery of critical data and applications. Speed and accuracy matters, as does privacy of sensitive data. Don’t compromise one or more for another when you are implementing BYOD Policy and Security measures.
2. Reduce Potential Security Threats
Network administrators must protect their wireless networks, data and internal systems against inbound attacks as well as rogue wireless devices. Administrative systems must be protected and isolated from end users who don’t require access to data. If they don’t need to go “there”, don’t allow them to do so. Give them the minimum access they need to complete their duties on a daily basis, and base their level of network access on their role with your organization. Think of security clearance at the Pentagon, how many closed doors will open by swiping your visitor’s badge? Probably not too many.
3. Consider Adding a Next Generation Firewall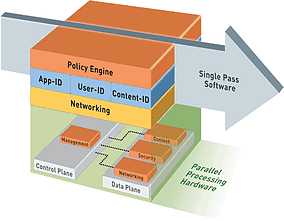
Preferably, one that can examine applications running on the hospital wireless network, as well as any potential incoming threats or rogue threats. Many organizations, including healthcare have budget constraints that often determine which solution is implemented. We take those limitations into consideration when we making our recommendations for organizations that are reviewing or implementing BYOD Policy and Security in Healthcare.
4. Increase Network Capacity
The abundance of new applications and video technologies that function on mobile devices such as laptops, tablets, and e-readers are emerging across all industries, adding additional stress to the hospital wireless network and those who manage them. You may have read more about the emergence of 802.11ac technology. From a cost perspective, some of the numbers may be high now but will level out with a more competitive playing field. The issue with 802.11ac as it stands now, is being sure to take into consideration the number of client devices currently on the market with 802.11ac capabilities. Many wireless access solutions are dual-channel - accepting clients connecting on 2.4ghz or 5ghz, but with 802.11n technology. The good news is that more clients are emerging daily and the right 802.11ac solution can operate effectively in environments where 802.11n still holds the majority. Again, operating capital may provide certain limitations, so it’s nice to have choices.
5. Bandwidth Utilization and Management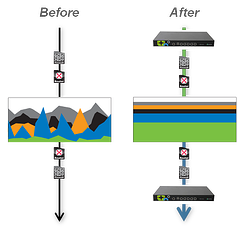
While bandwidth is currently in limited supply and demand continues to be high, healthcare organizations can take advantage of additional technologies available on the market today that help to manage what bandwidth is available. BYOD Policy and Security in Healthcare should be flexible to changing with the implementation of solutions that manage or shape and prioritize bandwidth allocation. While your organization may not currently be considering how streaming video or rich media can increase your profit margins, giving your staff the ability to utilize such services in a productive manner may open new doors. More effectively managing what is already in place may result in additional savings. Implementing policies that protect the mission-critical and administrative applications you care about most while limiting the traffic that is not high priority is a current best practice.
6. Maintain Flexibility
And we’re not just talking about flexibility that is good for your personal health. Being flexible in the design, creation and implementation of any BYOD Policy and Security Plan at your healthcare organization can allow for new and emerging technologies to be integrated. Writing good policy from the beginning that’s based on users and their level of access on any wireless network can make for faster implementations. The flexibility in the language can allow for last minute changes as well as the last minute integration when a new solution is determined to be a good fit for your hospital wireless network under any current policy.
7. See Your Policy in Action
You have the ability to see the words that are written in this post, so there’s no reason why you shouldn’t be able to see what is currently happening on your hospital wireless network. Wireless signals themselves are not visible to the naked eye, but new tools for visualization are on the market. There’s no reason to write a BYOD Policy and post it behind the toaster in the break room, 2 floors above your office and “hope” that everyone is compliant. In the literal sense, you should have the ability to see what is happening on your hospital wireless network, the location of wireless devices accessing the network, the applications they are utilizing and quickly audit or troubleshoot issues from the relative comfort of your desk...or even better, your own wireless device or tablet.
Chances are that the orange sash is going to stay retired no matter what changes you make to your wireless network. Remembering that safety patrol officer and the role that they played in keeping others safe from automotive threats may have inspired you to keep others safe and secure while a part of the growing BYOD trend.
If you’re considering BYOD implementation on your hospital wireless network, there’s a lot of planning involved, but it is worth it in the end. We are experts in BYOD integration and have worked with organizations all across the US implement successful and secure BYOD solutions. Contact us here with any questions or a free BYOD readiness consultation. We are always happy to help.