Network Access Control or NAC solutions have been around for years but have never really been adopted by most IT organizations out there. The reason most IT Managers never really jumped onto the NAC band wagon is because most of their machines were windows domain machines that they owned and controlled. This meant that they could already manage the end device with just the set of windows tools (group policy and network access protection).
So why introduce another NAC system that adds complexity in an all Windows world? The answer of course for most IT groups is “if it’s not broke, don’t fix it.”
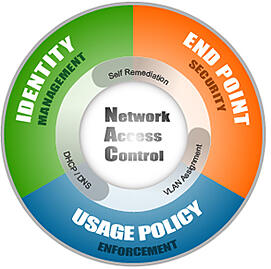
But fast forward to today’s Bring Your Own Device world. We no longer have windows domain machines to deal with, we've got as
many or more iOS and AOS devices as windows machines….and, as if we didn’t have enough to deal with, the users are almost all wireless.
At SecurEdge we design and install Wireless and Security systems all over the country. Is it any surprise that when we run usage reports for our clients on where the traffic is coming from (wired or wireless) that more than 75% of all internet bandwidth being consumed is from wireless users?
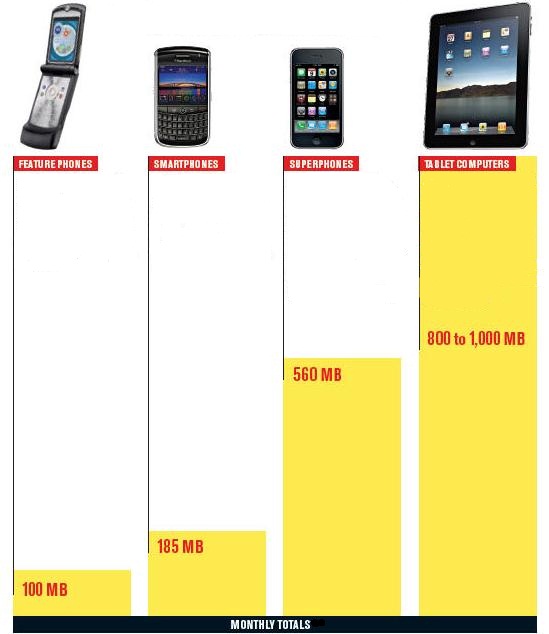
I should note that most of our clients are school systems and hospitals that have a large number of mobile users, but we’re seeing similar trends in the enterprise and even retail environment.
With that in mind, any organization concerned with network security or BYOD should consider implementing a NAC solution specifically engineered for mobile devices. We can go over more in depth details and get all your questions answered.
Here are the features you’ll need to enable BYOD with NAC:
1) Centralized Policy Management - no more having multiple systems to manage your different types of users. You need one place to see where Corporate Users, Guests, and Contractors are allowed to go.
2) Dashboard Device Profile Views - what types of devices are being used on your wireless network or wired network? Where are they connecting from? You’ll need to spot usage statistics and device details to know what network and policy decisions to make in the future.
3) Self-Registration of BYOD Devices - In Educational Technology, the average users has 3-5 mobile devices (iPad, Android Phone, Netbook, Gaming System, etc.). In the corporate environment you can figure 2.5 devices per person…which means putting your hands on each device isn’t feasible. Device Registration for BYOD should allow users to provision their own devices.
4) Secure Guest Registration & Access - thinking about just handing out a pre-shared key for guest access? If you do, the password will spread like wildfire to other guests and even employees. Today’s environment requires that you provide SECURE guest access. This means the user is allowed to register with a captive portal and the system will not provide a password to be shared around the office.
5) Remote Registration & Auto-provisioning of devices - How awesome would it be to email a college student BEFORE she gets to campus to let her register and auto-provision her device? You can do this today. The days of the freshman IT workshop day are over. Let them show up on campus ready to roll.
Use this features list as a guide to network access control features and get on the path to allowing pain free BYOD network access. SecurEdge Networks provides design, deployment and support of wireless and network access control solutions. You can register to speak to one of our consultants here, we also have a lot of free resources on the site we hope you’ll find useful.