Fast, secure WiFi—it’s what every business wants and needs today. Unfortunately, as technology has evolved, getting the performance and security you need has only become harder to achieve, maintain, and afford.
In the past, WiFi design involved a large emphasis on coverage, as only a select group of people used and relied on wireless to be productive—and content.
However, you will be hard pressed to find anyone—be it a guest, customer, employee, or student that doesn’t rely on wireless every day—and commonly while using multiple different devices.
With new 1:1 programs, BYOD, and new innovations like the Internet of Things (IoT), wireless systems have become a lot more complex to design, deploy and support.
Today’s wireless systems require a different set of features than they did in the past. Regardless of how big or small your business is, what industry, or how you’re planning on using your WiFi, there are certain components that every wireless network must include to guarantee both high-speed performance and air-tight security.
Let’s get started.
1. High Capacity Load Balancing 
Wireless networks were originally planned for coverage only, but with all the smartphones, tablets, laptops etc. out there--today’s wireless networks must be planned for capacity.
With the increased demand on both your wireless and wired infrastructure, you must incorporate high capacity load balancing.
This means, when one access point is overloaded, the system will actively shift users from one access point to another depending on the capacity that is available.
2. Scalability .jpg?width=268&name=scalabilty_(1).jpg)
The growth in popularity of new wireless devices will only continue to increase. Your network needs to have the ability to start small if necessary, but expand in terms of coverage and capacity as needed--without having to overhaul or build an entirely new network. Trust me, if you don’t need it now, you will need it later.
3. Network Management System
Modern day wireless networks are much more complex and may consist of hundreds or even thousands of access points, switches, firewalls, managed power and various other components.
You need to have a smarter way of managing the entire network from a centralized point. Deploying a network management system gives you that ability and so much more.
4. Role Based Access Control
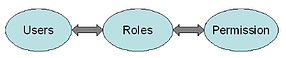
Role based access control (RBAC) allows you to assign roles based on who, what, where, when and how a user or device is trying to access your network.
Once the role of the device or end-user is defined, access control policies or rules can be enforced.
5. Indoor as well as Outdoor coverage options
Although you may feel you only need indoor WiFi at first, its possible that later you might need to add outdoor coverage as well.
For example, to parking lots, courtyards, etc. It's important that your wireless system has the capability of adding outdoor coverage, even after the fact.
6. The Ability to Measure Performance
With user expectations increasing, it's critical that you're continuously measuring performance from the end-users perspective. This means having the ability to see your end-users in real time, what type of devices they are using, what types of applications they are using, and the status of the different networking components that may affect the use of those devices. You should also have the ability to run proactive testing to help avoid potential problems before they happen.
7. Network Access Control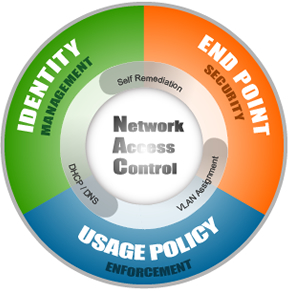.jpg?width=242&name=network-access-control-20111_(1).jpg)
Whether you refer to it as mobile device registration or network access control, it is essential to have a secure method for registering and securing the devices that you don't own.
Primarily, NAC controls the role of the user and enforces policies. Network access control can allow your users to register themselves to the network--a helpful feature that enhances the user experience.
8. Ability to communicate with both 2.4 GHz devices and 5 GHz devices
Baby scanners, blue tooth, microwaves, and many of today’s common use devices can interfere with users on 2.4 GHz devices--simply put, it’s a “crowded spectrum”. Since many devices still operate in that spectrum, you’ll need dual radio access points that can manage users on both 2.4 GHz and 5 GHz at the same time.
9. Web Content/Application Filtering.jpg?width=287&name=download_(1).jpg)
More than ever before, network security must become application aware in order to alleviate threats.
You should have application filtering in place in order to protect users from content that might contain malicious threats as well as to prevent possible performance issues.
10. Mobile Device Management
Think about how many mobile devices will be accessing your wireless network; now think about the thousands of applications you’re going to have running on those mobile devices.
How do you plan on managing all of this, especially as devices come and go from your business.
Mobile device management can provide control of how you will manage access to applications and programs. You can even remotely wipe the device if it’s lost or stolen.
11. Application Prioritization
Application prioritization is exactly what it sounds like; it's the ability to guarantee performance levels to applications that you have selected as mission-critical.
This means your business can ensure that the applications that are most important to your operations have exactly what they need to function at a high-level, even as other less critical applications are accessing the network at the same time.
Without application prioritization there is no way to control the balance between business applications and recreational applications, and no way to ensure that your mission-critical processes and systems maintain the performance they need--in other words, it would be chaos.
12. Roaming
You shouldn't have to worry about dropped connections, slower speeds or any disruption in service as you move throughout your office or even from building to building—wireless needs to be mobile-first..
Mobile devices are just that, mobile, meaning your users will expect to maintain the same level of performance no matter where they are or if they are on the move.
Planning for WiFi today means planning for roaming. Roaming allows your end-users to successfully move from one access point to another without ever noticing a dip in performance.
For example, allowing a student to check their Facebook news-feed as they walk from one class to the next.
13. Redundancy
“Downtime” is a productivity and moral killer—if the WiFi goes down everything comes to a grinding stop.
The level or amount of redundancy your WiFi system requires depends on your specific environment and needs.
For example, a hospital environment will need a higher level of redundancy than say a coffee-shop, however, at the end of the day they both need to have a back-up plan in place.
14. Adaptive Radio Management
Technical expertise is both expensive and hard to find; it takes years of training and experience to know how to get it right—that’s time and money most businesses just don’t have.
Adaptive radio management or ARM, is like having an RF or WiFi expert on site that helps to maximize performance for your end-users.
It does this by collecting RF data from your access points and then using that data to make intelligent decisions about power levels, channels, air-time fairness, client-loads and even roaming.
*It should be noted that while ARM can be a powerful tool to help fix RF issues, it’s not a magic wand—nothing can replace having a proper wireless network design.
15. Proper Security Means Using the Right Firewall
Building an “air-tight” network doesn’t come down to just one component alone; it’s about many components all working together just right to keep your data and your end-users safe.
 However, the backbone of that system is your network firewall. For example, with the right firewall in place you’ll be able to:
However, the backbone of that system is your network firewall. For example, with the right firewall in place you’ll be able to:
- See and control both your applications and end-users
- Create the right balance between performance and security
- Reduce complexity with baked-in features such as:
- Anti-virus protection
- Spam filtering
- Deep packet inspection (DPI)
- Application filtering
- Protect your network and end-users against known and unknown threats including:
- Ransomware
- Encrypted malware
- Zero-day
- Malicious botnets
16. Switching
Basically, a network switch is the traffic cop of your network—making sure that everyone and every device gets to where they need to go.
They’re an essential part of every fast, secure wireless network for several reasons:
- They help the traffic on your network flow more efficiently
- They minimize unnecessary traffic
- They create a better user experience by ensuring your traffic is going to the right places.
In many cases, performance issues arise from bottlenecks or choke points caused by using the wrong type of switch or from outdated switches.
Whether you’re updating your current wireless system or deploying wireless for the first time, you can’t ignore or forget about your switching.
17. 802.11ac Access Points
Finally, we get to your access points. Access points are one of the most well-known components within your entire system—they’re the lead singer if you will.
There are many different types of APs available from a variety of different manufacturers. However, no matter which route you go, you need to make sure your APs are at the very least 802.11ac—currently Wave 2.
From there, it gets a little bit more complicated. There are many factors that will impact the performance of your access points, from the amount deployed, their configuration, and even your wired infrastructure.
Putting It All Together
Your network infrastructure is a system—made up of many different components that must come together just right to produce the best results.
Ultimately, it doesn’t matter what products you choose to deploy--if your WiFi Design is bad, nothing will function properly.
Even if you have a wireless solution that works well now—things inevitably change. The RF environment, number of devices, types of devices, and how your end-users use the WiFi.
Everything changes over time because wireless is by nature, dynamic.
This leads us to our next challenge.
From both a technical and financial perspective, “How do you plan on keeping up with demand and the constant evolution of technology?”
Using a monthly subscription, WiFi as a Service solves these problems. WaaS allows businesses of any type or size to budget over-time, exactly what they need to provide the best class of service to their end-users.
Some of the benefits include:
- Monthly payments
- Scalability up or down to fit your changing requirements
- Deployment of the latest technology
- Freedom to use your budget on other mission-critical projects
Managed WiFi networks are nothing new, however, with WiFi as a Service we’re finally able to incorporate both technical expertise and proper design with a financial model that makes WiFi available to everyone.
A common saying around the office is that, WiFi is a utility like electricity—it’s a “must-have” for every business today.




