As we move closer toward the digital future, we create for ourselves a hundred new ways to share information, experiences and knowledge. We are seemingly never alone- as long as you have a device and network connectivity, you've got seemingly endless possibilities to connect and share.
From a satellite office on the other side of the world, you can share presentations with colleagues, onboard new employees into payroll and benefits, send your mom a fruit arrangement because you said you'd call but lost track of time, and catch the last 30 minutes of the the Croatia v Russia game as you chug coffee between meetings. All of this information is being created, saved and shared via wireless network. With all of this important private information being hosted on the internet, its paramount that it be secured. While there are many important things to consider when designing a secure WiFi network, there are a few factors that have a major impact on your network security. Here are 4 major factor to consider when building a secure wireless network and how wifi security can protect you in the future:
Mobility Security
As devices get smaller and network coverage areas grow wider, it is important to design a wireless network that is mobility first. Whether its students walking across campus to their next lecture, healthcare providers shuffling between offices and patient rooms, or warehouse crew members relying on barcode scanners to inventory new orders, having a seamless wireless experience is paramount. Equally as important, is the security of those devices and users connecting to the network.
At SecurEdge, we put mobility first, meaning we will design a wireless network infrastructure based on your unique criteria so that users and devices have the coverage and performance they need wherever they are. In doing, so we also create unique opportunities to secure those devices. Through Role Based Access Control and Load Balancing, we can complicate your network and make it more difficult for hackers to attack. We will segment your traffic into different lanes and allow you to control how and what users can access your network. We will also program your hardware to balance out device usage across your access points so that coverage is evenly distributed, users have the highest possible quality of network speed, and you don’t leave an AP overloaded and vulnerable. Our RF designs also have a high degree of redundancy built in, so if there are any complications, your network has the backup to keep running.
IoT Security
The Internet of Things is booming, putting a lot of strain on wireless network systems that were not designed with these devices in mind. It is predicted that by 2020, there will be 24 billion IoT devices. These include personal devices like wearables and hardware applications like security devices and environmental control devices. They are taking over every industry and shaping the way we live and interact with our environments. In the healthcare field, IoT is already being used to help nurses monitor patient vitals and activity, such as when they leave their bed. In hospitality, smart laundry services are popping up everywhere, informing users when their laundry is ready, letting them pay for services through convenient apps and keeping their belonging secure. Government offices, university campuses, large enterprises, and private homes, are switching to IoT devices like Nest for security and temperature control. Warehouses and distribution centers rely on barcode scanners and communication devices to ensure safety and reliability.
Securing an ever growing network of IoT devices may seem like an uphill battle, but with SecurEdge WiFi as a Service, not only will you get a wireless network design that is security first, you'll get ongoing software updates, 24/7 network monitoring and monthly health reports to give you insight into your network and alert you of any problems that occur. With our Edge Manage Software, you'll have visibility into your network like never before: view real-time analytics and live heat maps to see the health and security to help you troubleshoot problems with your IoT devices and prevent WiFi security threats before they happen.
BYOD Security
Today, Bring Your Own Device (BYOD) is not a question but a statement. Schools, offices, hospitals, they all now encourage rather than detract users from bring their own devices. Why? As technology advances, we see more and more the advantages and convenience they can provide. Whether its iPads in the classroom helping teachers share documents and grades with students or nurses using wearables to communicate quickly with faculty and staff, its becoming standard for work places to except the once bothersome BYOD.
The one question surrounding BYOD that hasn't changed, is whether or not its secure. Can allowing potentially hundreds of outside devices into your building and onto your wireless network put a dangerous strain on your resources that leaves you susceptible to network failure? Can you really track and monitor so many unknown devices in your coverage area and continue to protect your authorized users and devices from security threats? The answer is, with the right wireless network design, absolutely. Role Based Access Control is the primary defender against BYOD security threats. We always make RBAC a part of our network security solution, and we'll work with you to determine how you want to organize your user and what permissions you want to grant.
Cloud Security
Remember the days before autosave? When a document could just disappear into nothingness after an accidental tap of the close button when you meant to hit minimize, or when you were so involved in your work you failed to notice the draining battery life and then lunged toward your charger, clumsily stuffed it into your computer only for the screen to go blank, losing all of you hard work? *Shutters* Thanks to Cloud technology, these problems that once plagued us now seem a laughable part of our canon. Don’t get too relaxed though, while the cloud has made it easier than ever to save, store and share information, it has made in even easier for hackers to access that information.
To protect yourself and your private data from data hacking, you need to start with a safe, secure and reliable wireless network connection. SecurEdge designs wireless network infrastructures with network security at the base. Cloud based platforms like Salesforce, G Suite, and Amazon Web Services are used by millions of companies worldwide and all depend on reliable network security to house and protect volumes of personal data. We will program your network to utilize multiple layers of user permissions, build in redundancy to prevent problems before they occur, supply you with the right amount of hardware in the right places so your network is never overwhelmed, and use only the highest quality firewall devices available so that you have all the network security bases covered.
How Does SecurEdge provide Network Security?
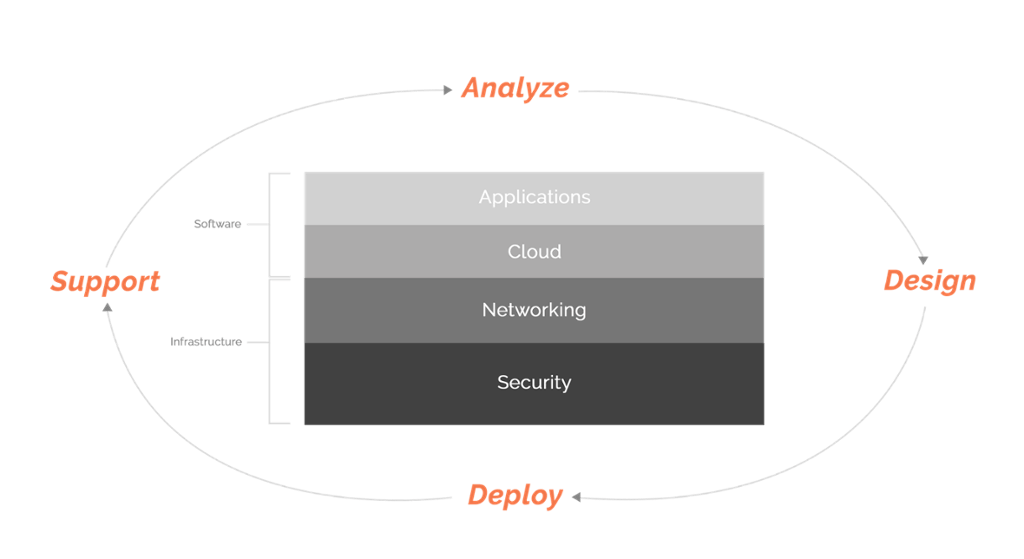
SecurEdge incorporates Network Security into your Wireless Network Design in 4 stages:
Analyze
We will analyze your current network security needs, whether we are assessing an existing network or planning for a new one. We examine the environment, applications and devices to determining your wireless network and wifi security needs. Then we'll take your info to the lab and using our industry expertise and hardware, prepare the right solution for your environment.
Design
Once we have a plan, we will begin a design, using the floor plans you've provided or in the case you don't have access to those, intelligent predictive design based software configured based on industry knowledge. Our team of expert engineers will design a wireless network infrastructure built on the foundation of security. We will walk you through your design and answer any questions or concerns you have.
Deploy
Installation is a crucial step in ensuring wireless network security. The simplest mistake, like placing an AP too high can weaken your network and leave it vulnerable. Whether we deploy your systems or you use one of our trusted contractors, SecurEdge guarantees that your system will be installed right the first time.
Support
After your network infrastructure is deployed, we will provide continuous support so that you have peace of mind knowing that your network is secure. As part of our Managed Network Services, you’ll receive ongoing software updates for all of your hardware so that you are always on the cutting edge of device security, 24/7 network monitoring and alerts when threats are detected, and monthly health updates to keep you informed on the status of your network security.
At SecurEdge, security is the foundation of our wireless network solution stack. Whether we are designing a network infrastructure for a new space, overhauling an existing network, or just providing managed services, we are doing so with security first. There are a number of solutions we can provide to give your organization control of your applications, users and content. These include things like malware scans, web content filtering, network security analysis, next generation firewalls and more. We’ll design a network solution that is security first and give you the tools and resources to manage the network long after its been deployed.
Ready to get started? Contact Us.




